The Bits Must Flow: (Net)Working through the abstractions
A presentation at Cloud-Native Rejekts NA 2022 in in Detroit, MI, USA by fen aldrich

The Bits Must Flow (net)Working through the abstractions 1 — @CrayZeigh
What happens when you visit a website? 2 — @CrayZeigh Start with a classic Audience Participation
Why DNS? 3 — @CrayZeigh

167,069GB Internet Traffic Per Second 1 https://interenetlivestats.com/one-second/#traffic-band 4 — @CrayZeigh 1
1,336,544,000,000,000 bits per second 5 — @CrayZeigh

6 — @CrayZeigh

OSI 7-Layer model Application Presentation Session Transport Network Data Link Physical 7 — @CrayZeigh
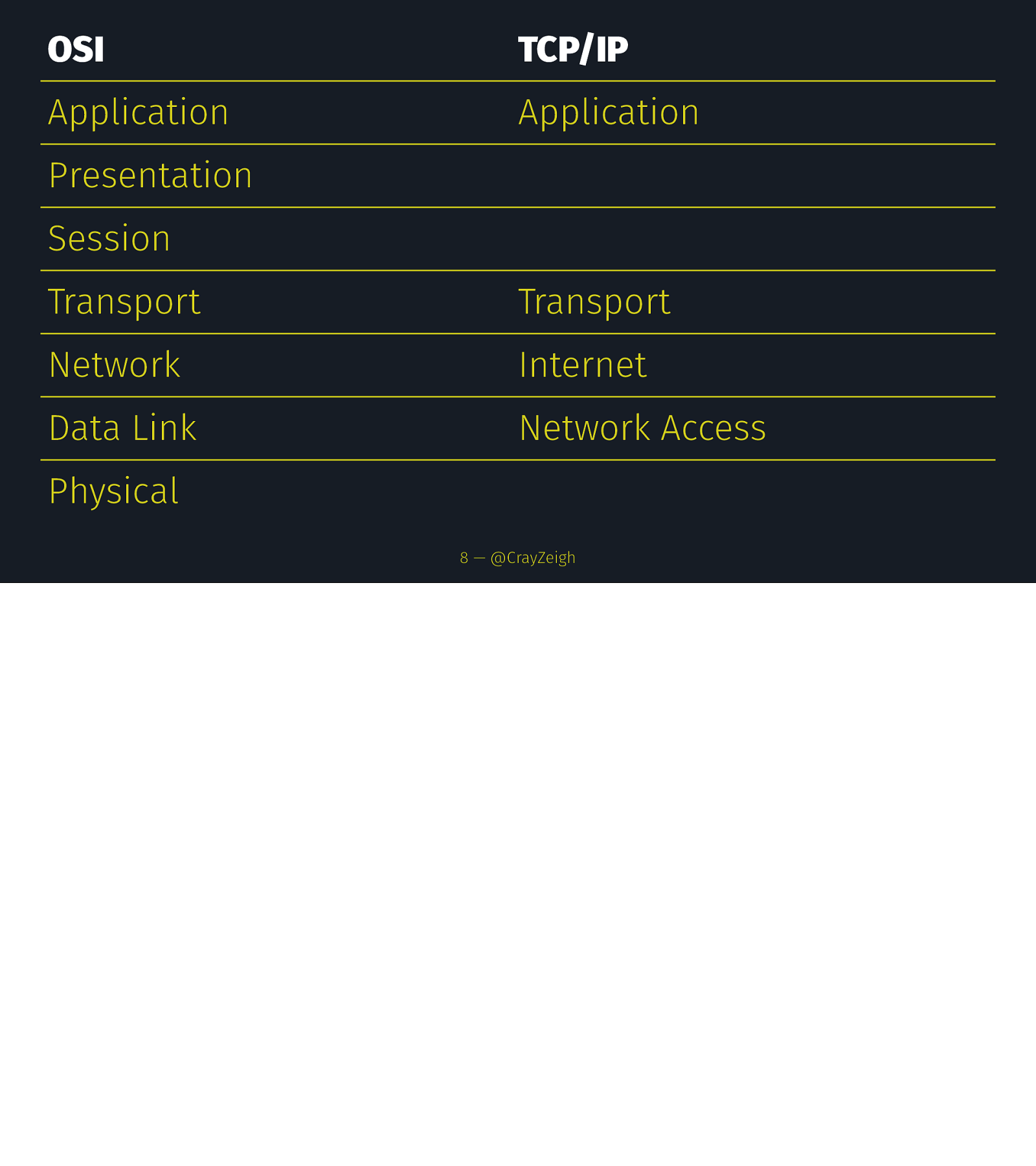
OSI TCP/IP Application Application Presentation Session Transport Transport Network Internet Data Link Network Access Physical 8 — @CrayZeigh
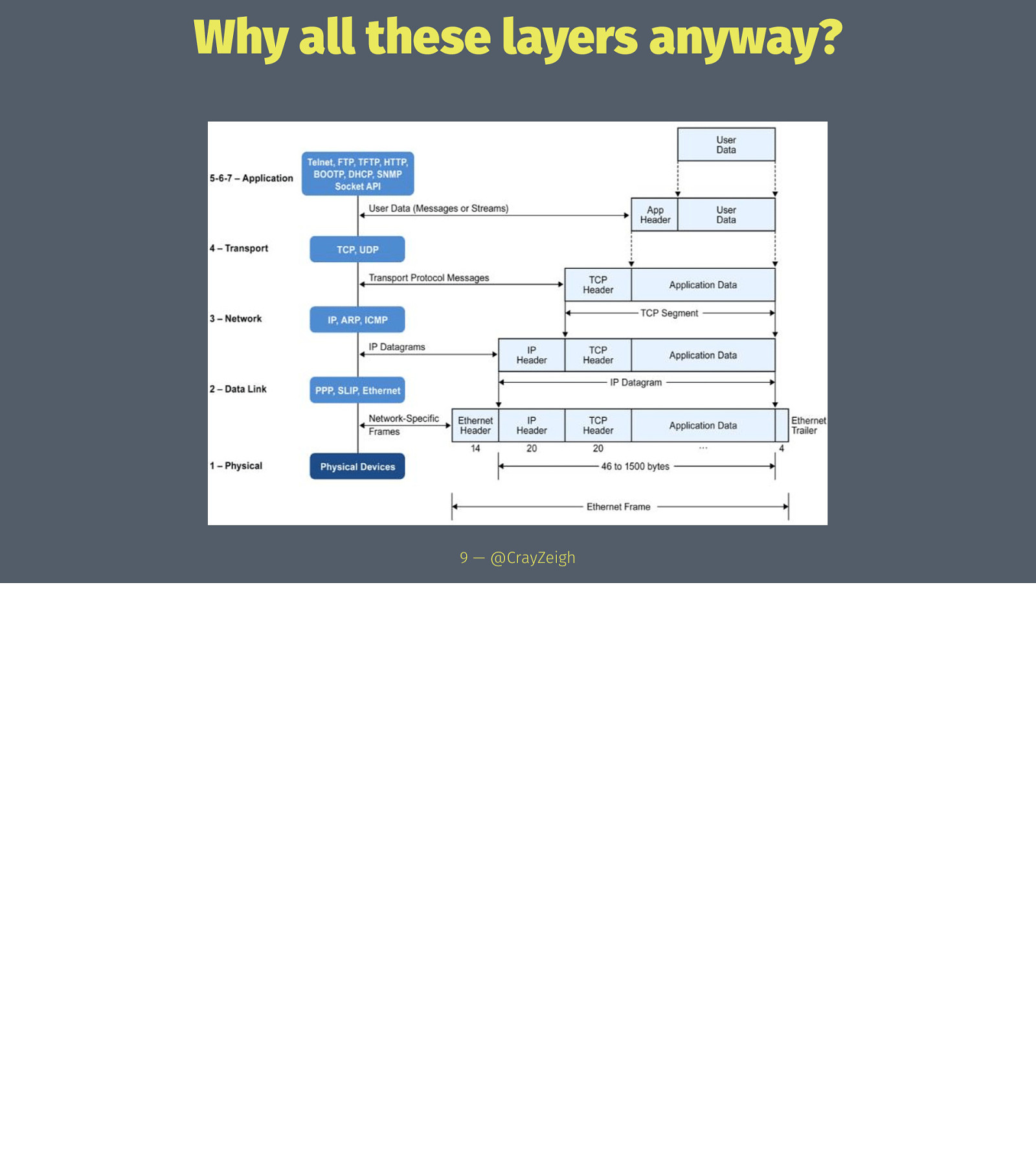
Why all these layers anyway? 9 — @CrayZeigh

Network Access: Data Frames help translate digital to physical 10 — @CrayZeigh
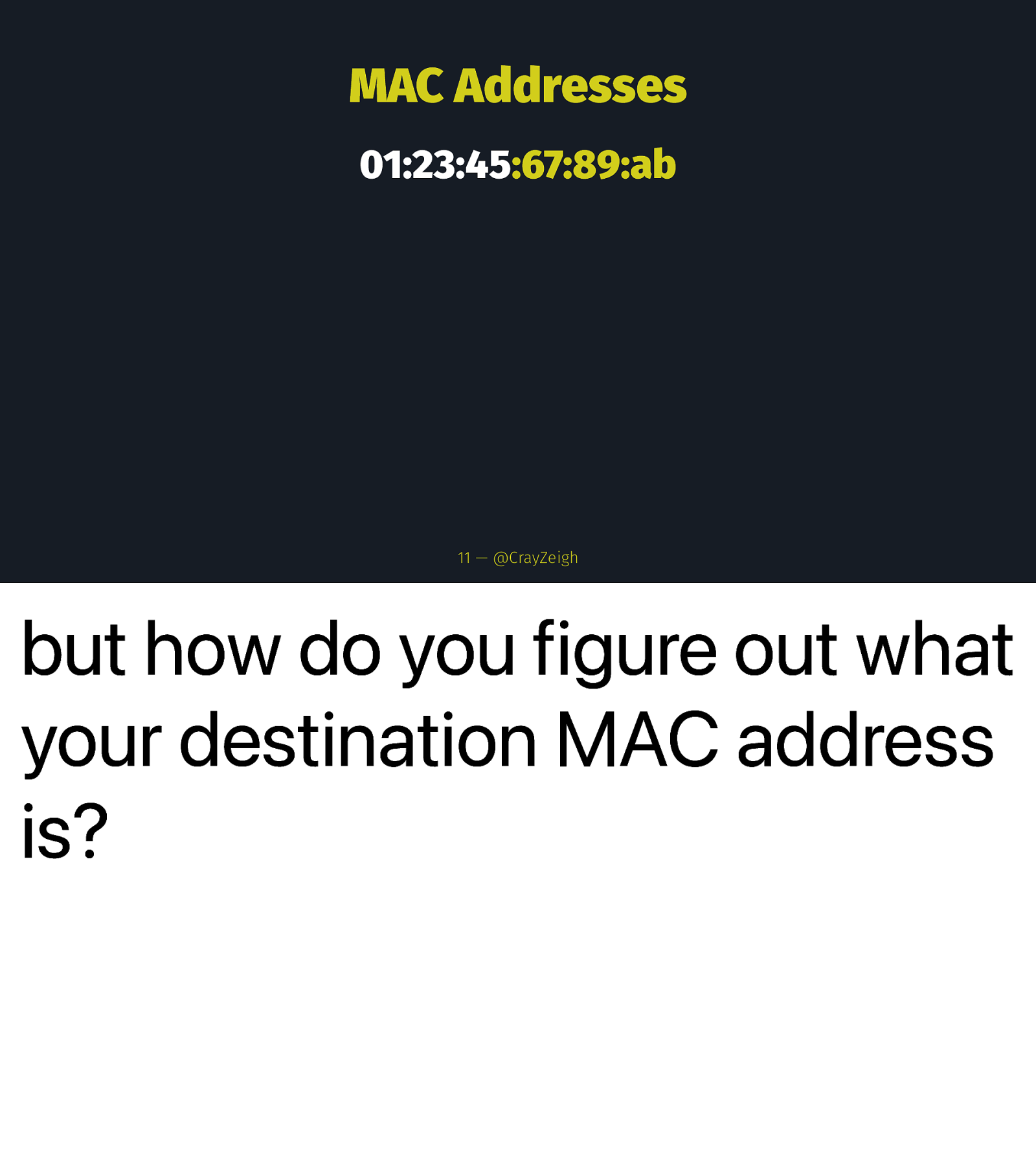
MAC Addresses 01:23:45:67:89:ab 11 — @CrayZeigh but how do you figure out what your destination MAC address is?
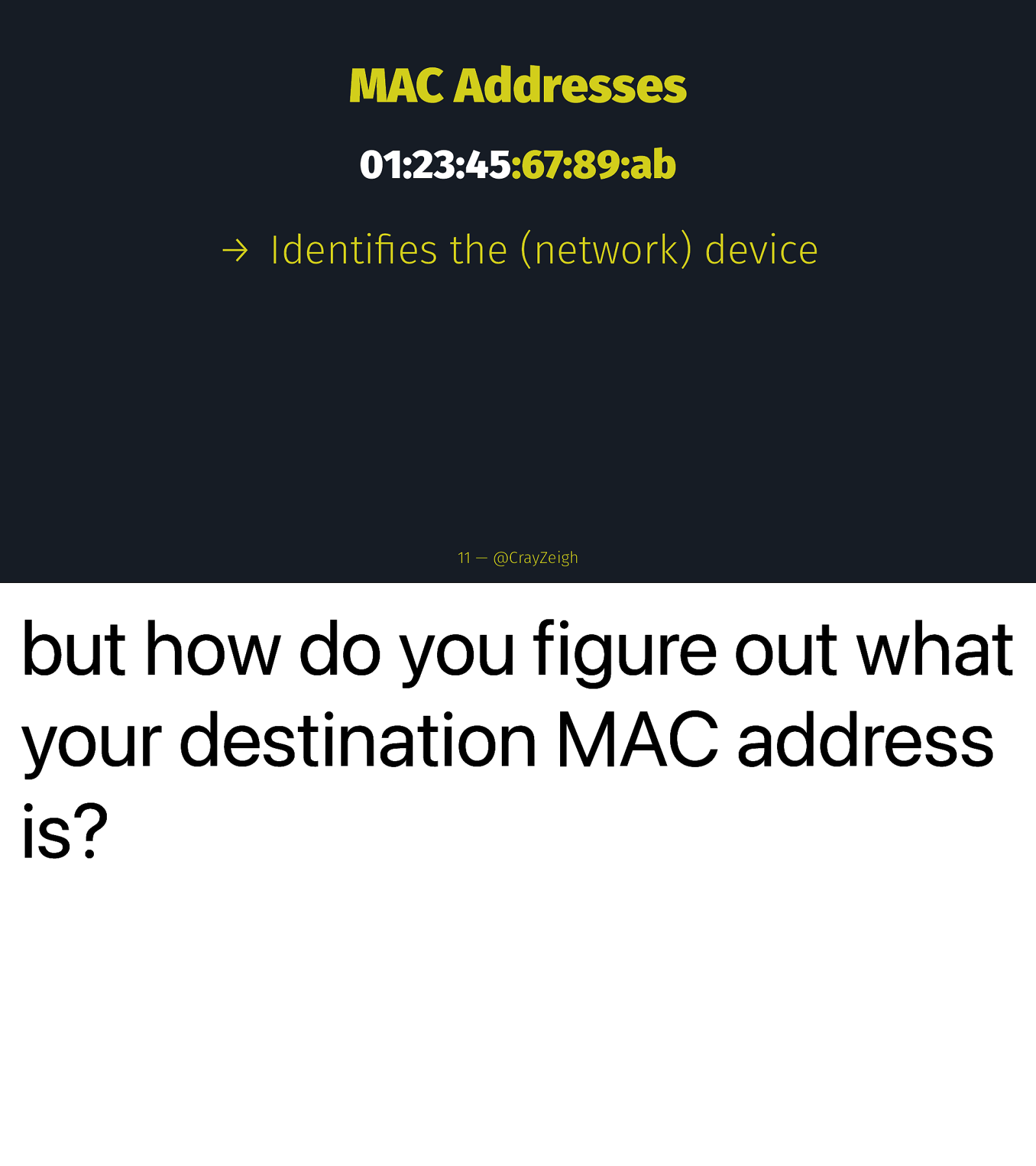
MAC Addresses 01:23:45:67:89:ab → Identifies the (network) device 11 — @CrayZeigh but how do you figure out what your destination MAC address is?
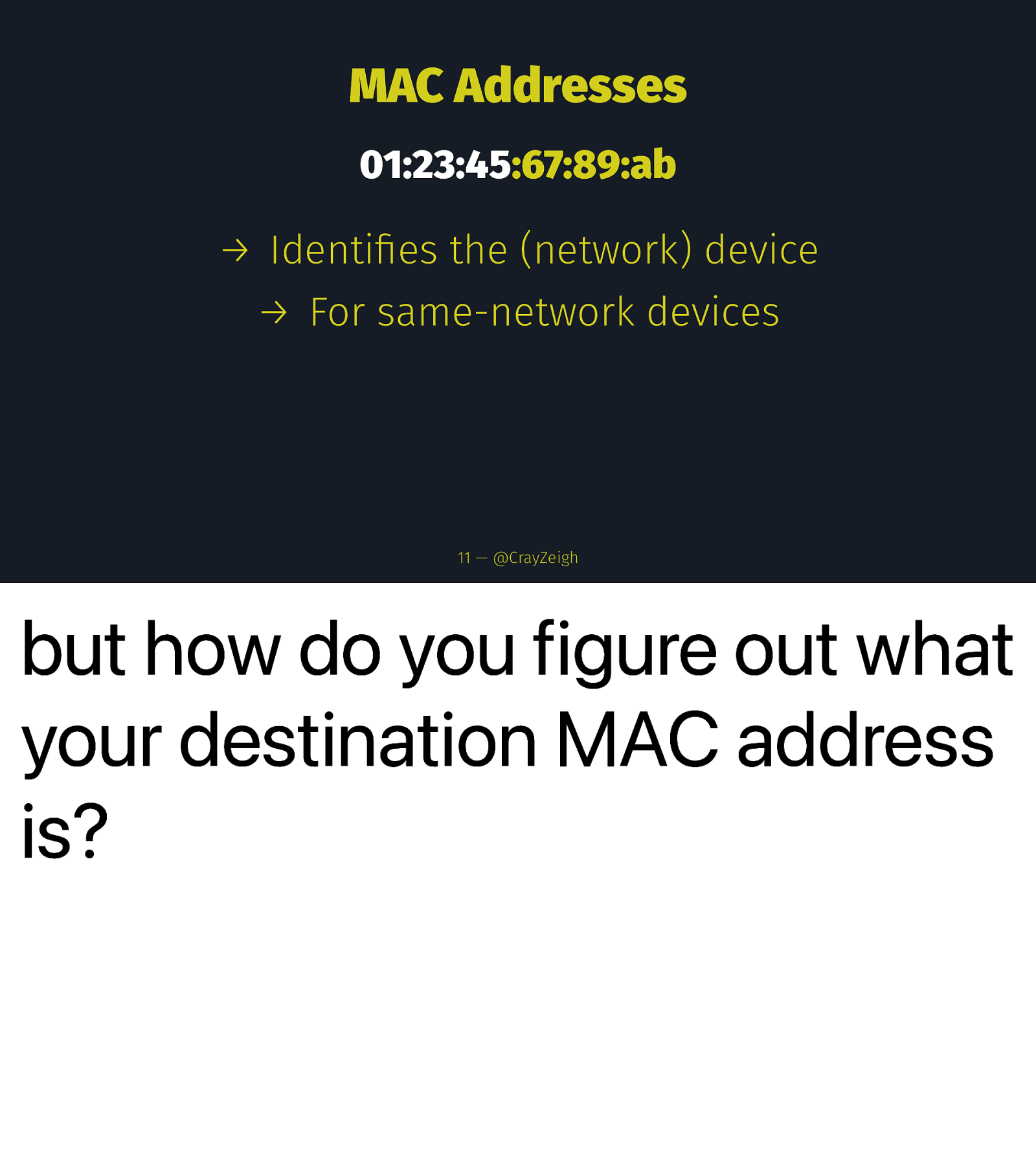
MAC Addresses 01:23:45:67:89:ab → Identifies the (network) device → For same-network devices 11 — @CrayZeigh but how do you figure out what your destination MAC address is?
ARP 2 2 Address Resolution Protocol 12 — @CrayZeigh arp -a need a way to separate traffic
ARP 2 → Mapping IPs and MAC addresses 2 Address Resolution Protocol 12 — @CrayZeigh arp -a need a way to separate traffic
ARP 2 → Mapping IPs and MAC addresses → Broadcasts to find neighbors 2 Address Resolution Protocol 12 — @CrayZeigh arp -a need a way to separate traffic
VLANs 13 — @CrayZeigh Broadcast & Switchs v Hubs
VLANs → Limiting Broadcast Domains 13 — @CrayZeigh Broadcast & Switchs v Hubs
VLANs → Limiting Broadcast Domains → IEEE 802.1q 13 — @CrayZeigh Broadcast & Switchs v Hubs
VLANs → Limiting Broadcast Domains → IEEE 802.1q → up to 4096 VLANs 3 3 VXLAN addresses this but that’s A Whole Other Thing 13 — @CrayZeigh Broadcast & Switchs v Hubs
VLANs → Limiting Broadcast Domains → IEEE 802.1q → up to 4096 VLANs 3 → Native or Tagged 3 VXLAN addresses this but that’s A Whole Other Thing 13 — @CrayZeigh Broadcast & Switchs v Hubs
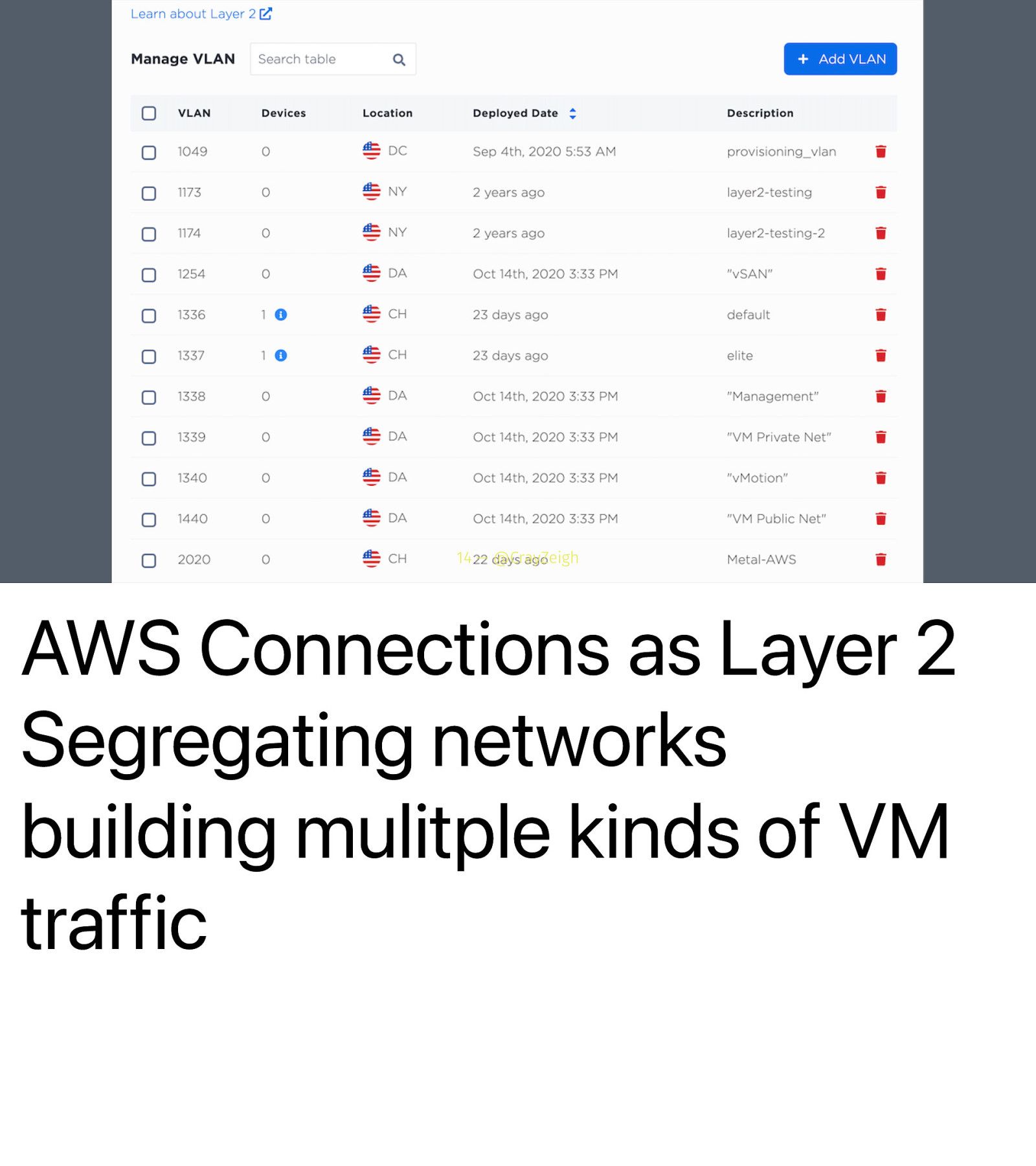
14 — @CrayZeigh AWS Connections as Layer 2 Segregating networks building mulitple kinds of VM traffic
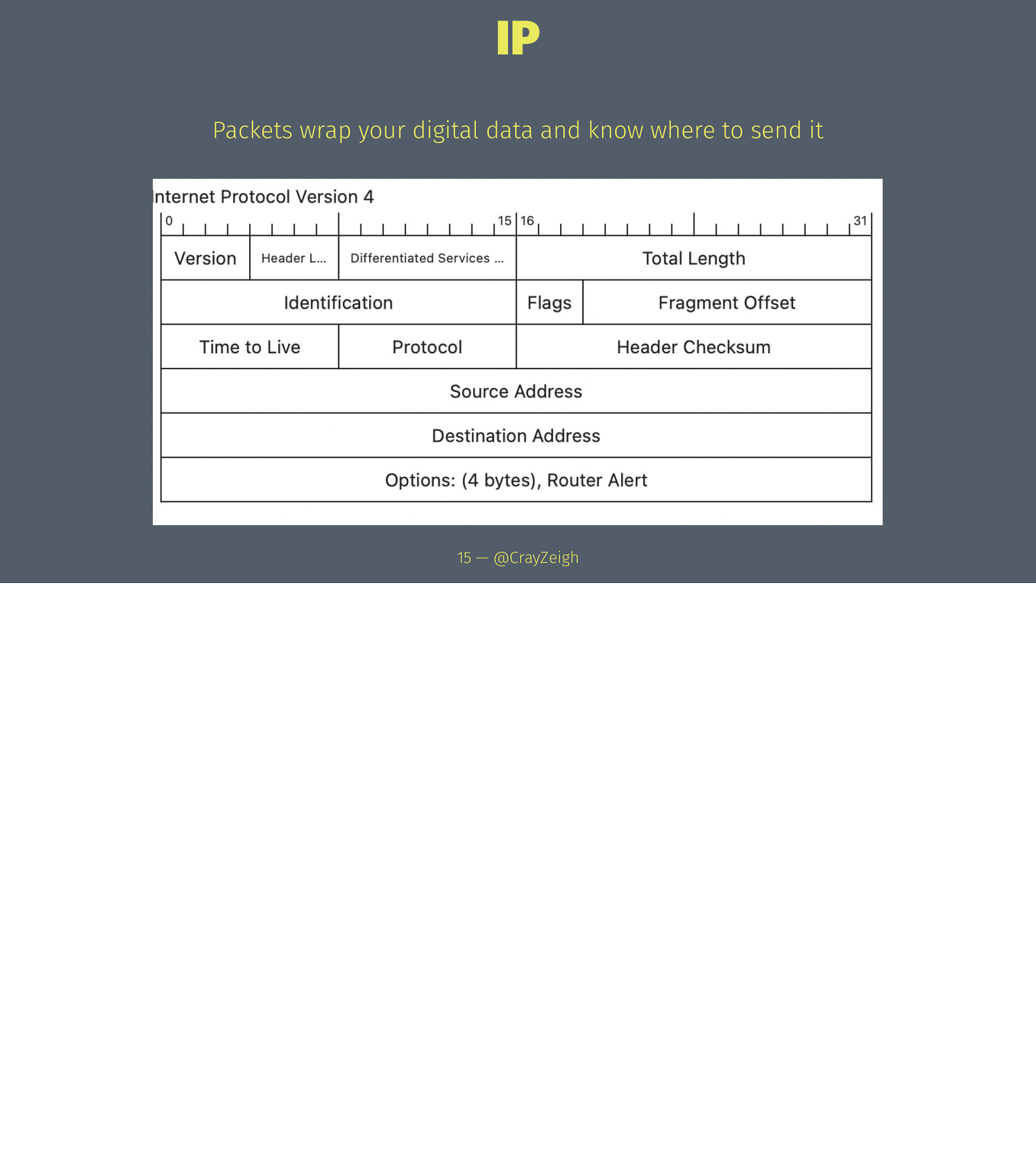
IP Packets wrap your digital data and know where to send it 15 — @CrayZeigh
Classes & CIDR 16 — @CrayZeigh Probably never really dealt with Classed IP addresses though there is some holdover in the reserved private IP space, 10.x, 172.16.x - 172.31.x, 192.168.x ^ Previously given classed space you could have C (256), next up B (65k) and A (16.8m)
Classes & CIDR → Classess Inter Domain Routing 16 — @CrayZeigh Probably never really dealt with Classed IP addresses though there is some holdover in the reserved private IP space, 10.x, 172.16.x - 172.31.x, 192.168.x ^ Previously given classed space you could have C (256), next up B (65k) and A (16.8m)
Classes & CIDR → Classess Inter Domain Routing → Replaced previous “class a/b/c” IP addressing to help address IP address availability 16 — @CrayZeigh Probably never really dealt with Classed IP addresses though there is some holdover in the reserved private IP space, 10.x, 172.16.x - 172.31.x, 192.168.x ^ Previously given classed space you could have C (256), next up B (65k) and A (16.8m)

Classes & CIDR → Classess Inter Domain Routing → Replaced previous “class a/b/c” IP addressing to help address IP address availability → Helps determine destination locality i.e. routing 16 — @CrayZeigh Probably never really dealt with Classed IP addresses though there is some holdover in the reserved private IP space, 10.x, 172.16.x - 172.31.x, 192.168.x ^ Previously given classed space you could have C (256), next up B (65k) and A (16.8m)

CIDR Notation 17 — @CrayZeigh
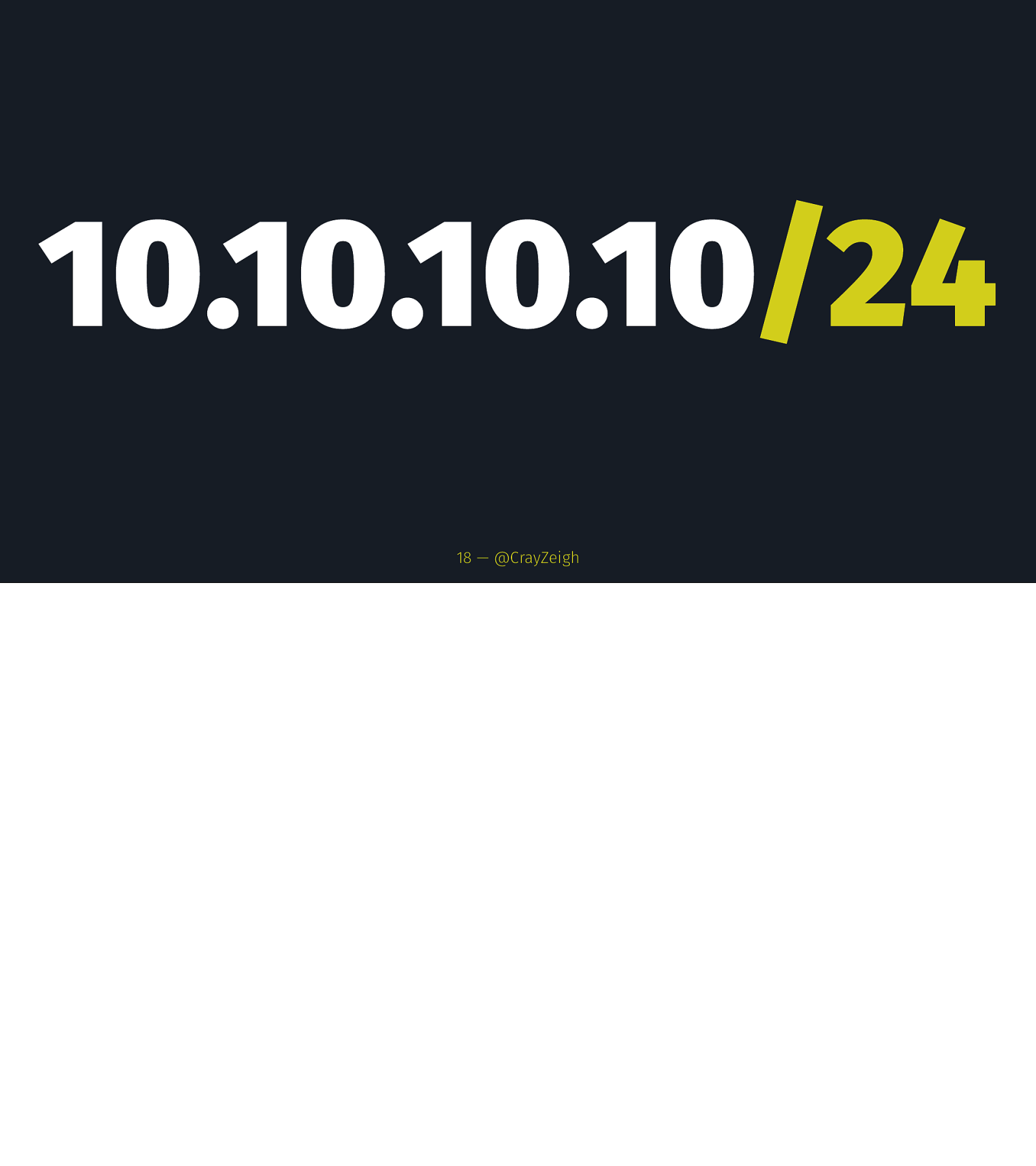
10.10.10.10/24 18 — @CrayZeigh

IP Address/Network Bits 19 — @CrayZeigh

IP: 10.10.10.10 SM: 255.255.255.0 20 — @CrayZeigh

Converts to Binary: IP: 00001010.00001010.00001010.00001010 SM: 11111111.11111111.11111111.00000000 in Subnet Mask: 1s = Network Space 0s = Host Space 21 — @CrayZeigh

Special IPs 22 — @CrayZeigh Not aobut private, multicast or research IPs that’s a different thing Think of “network” as “any for routing purposes this cannot be used in any other way

Special IPs → Broadcast (10.10.10.255) 22 — @CrayZeigh Not aobut private, multicast or research IPs that’s a different thing Think of “network” as “any for routing purposes this cannot be used in any other way
Special IPs → Broadcast (10.10.10.255) → Host bits all 1 22 — @CrayZeigh Not aobut private, multicast or research IPs that’s a different thing Think of “network” as “any for routing purposes this cannot be used in any other way

Special IPs → Broadcast (10.10.10.255) → Host bits all 1 → Network (10.10.10.0) 22 — @CrayZeigh Not aobut private, multicast or research IPs that’s a different thing Think of “network” as “any for routing purposes this cannot be used in any other way
Special IPs → Broadcast (10.10.10.255) → Host bits all 1 → Network (10.10.10.0) → Host bits all 0 22 — @CrayZeigh Not aobut private, multicast or research IPs that’s a different thing Think of “network” as “any for routing purposes this cannot be used in any other way
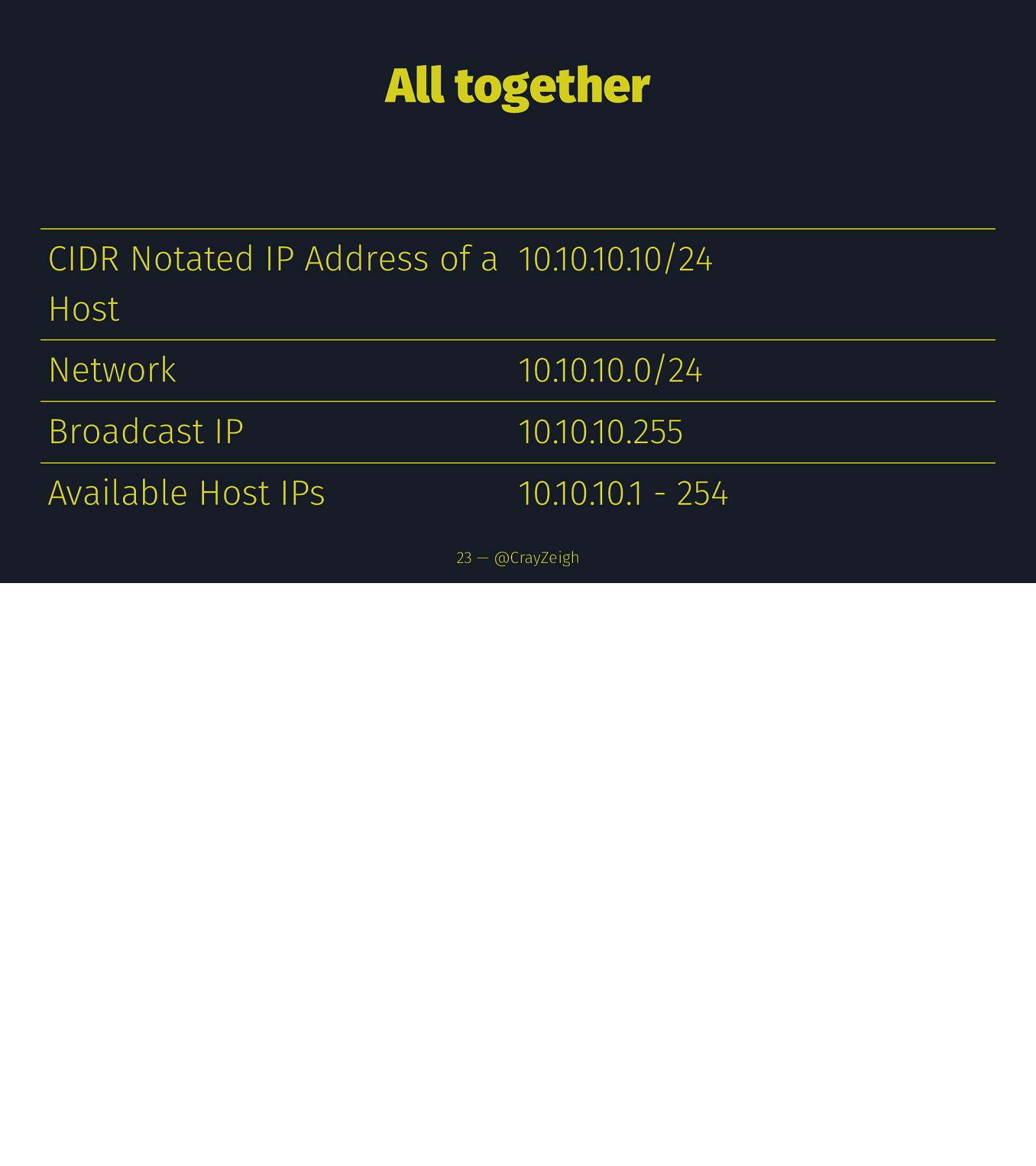
All together CIDR Notated IP Address of a 10.10.10.10/24 Host Network 10.10.10.0/24 Broadcast IP 10.10.10.255 Available Host IPs 10.10.10.1 - 254 23 — @CrayZeigh
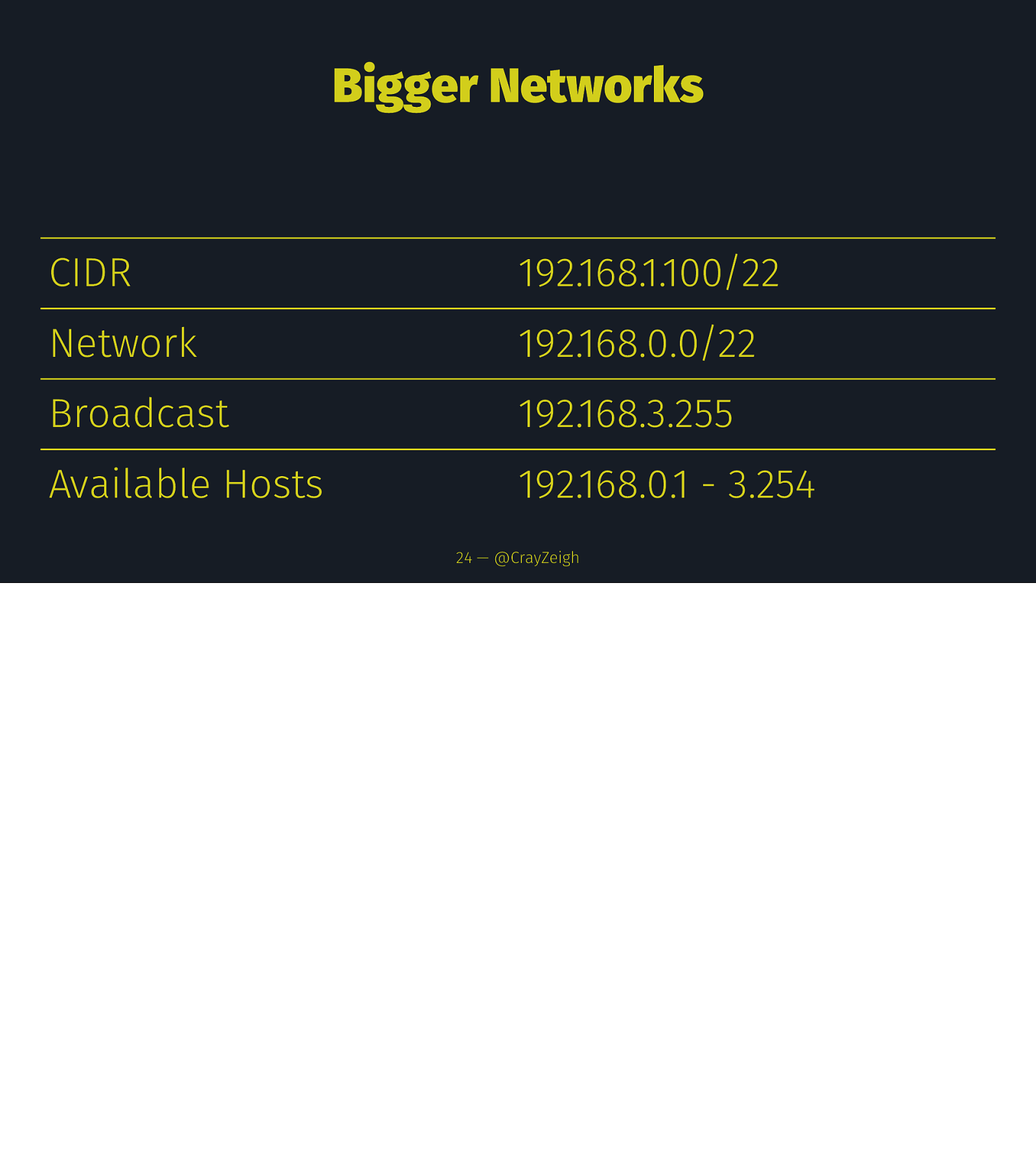
Bigger Networks CIDR 192.168.1.100/22 Network 192.168.0.0/22 Broadcast 192.168.3.255 Available Hosts 192.168.0.1 - 3.254 24 — @CrayZeigh
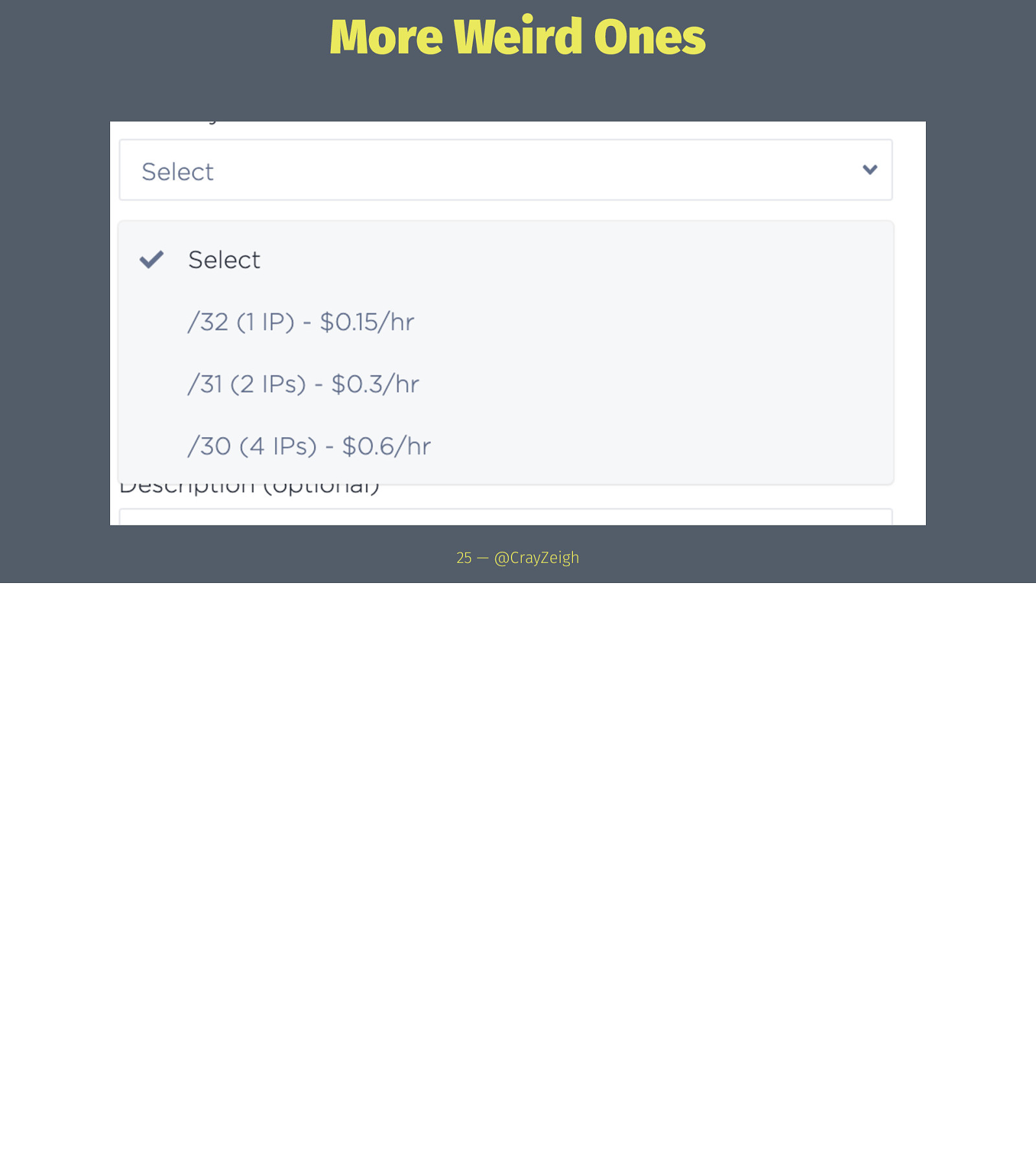
More Weird Ones 25 — @CrayZeigh

Weird Ones Explained 26 — @CrayZeigh

Weird Ones Explained → /30 26 — @CrayZeigh

Weird Ones Explained → /30 → Costs 4 IPs, but only grants 2 hosts 26 — @CrayZeigh

Weird Ones Explained → /30 → Costs 4 IPs, but only grants 2 hosts → Broadcast & Network still apply 26 — @CrayZeigh

Weird Ones Explained → /30 → Costs 4 IPs, but only grants 2 hosts → Broadcast & Network still apply → Might use today for compatibility reason or because you like IP addresses 26 — @CrayZeigh

Weird Ones Explained 27 — @CrayZeigh

Weird Ones Explained → /31 27 — @CrayZeigh
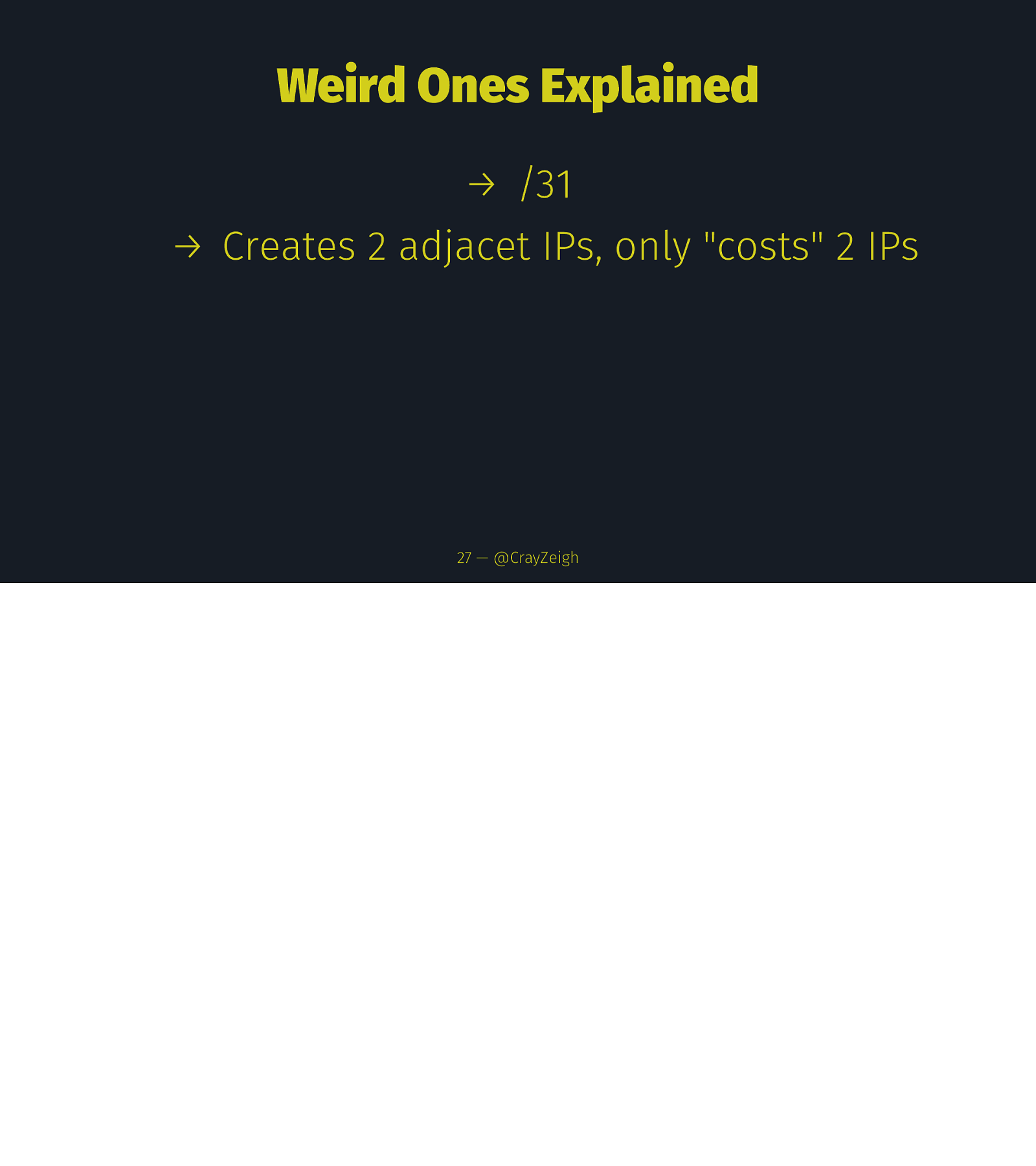
Weird Ones Explained → /31 → Creates 2 adjacet IPs, only “costs” 2 IPs 27 — @CrayZeigh
Weird Ones Explained → /31 → Creates 2 adjacet IPs, only “costs” 2 IPs → Proposed in RFC3021 in 2000(!) to combat dwindline IP availability 27 — @CrayZeigh

Weird Ones Explained 28 — @CrayZeigh Anycast App Idea
Weird Ones Explained → /32 28 — @CrayZeigh Anycast App Idea
Weird Ones Explained → /32 → Single IP address 28 — @CrayZeigh Anycast App Idea
Weird Ones Explained → /32 → Single IP address → still very useful mainly for additional or public IPs 28 — @CrayZeigh Anycast App Idea
Routing Source: 10.10.10.10/24 Destination: 10.10.10.100 29 — @CrayZeigh
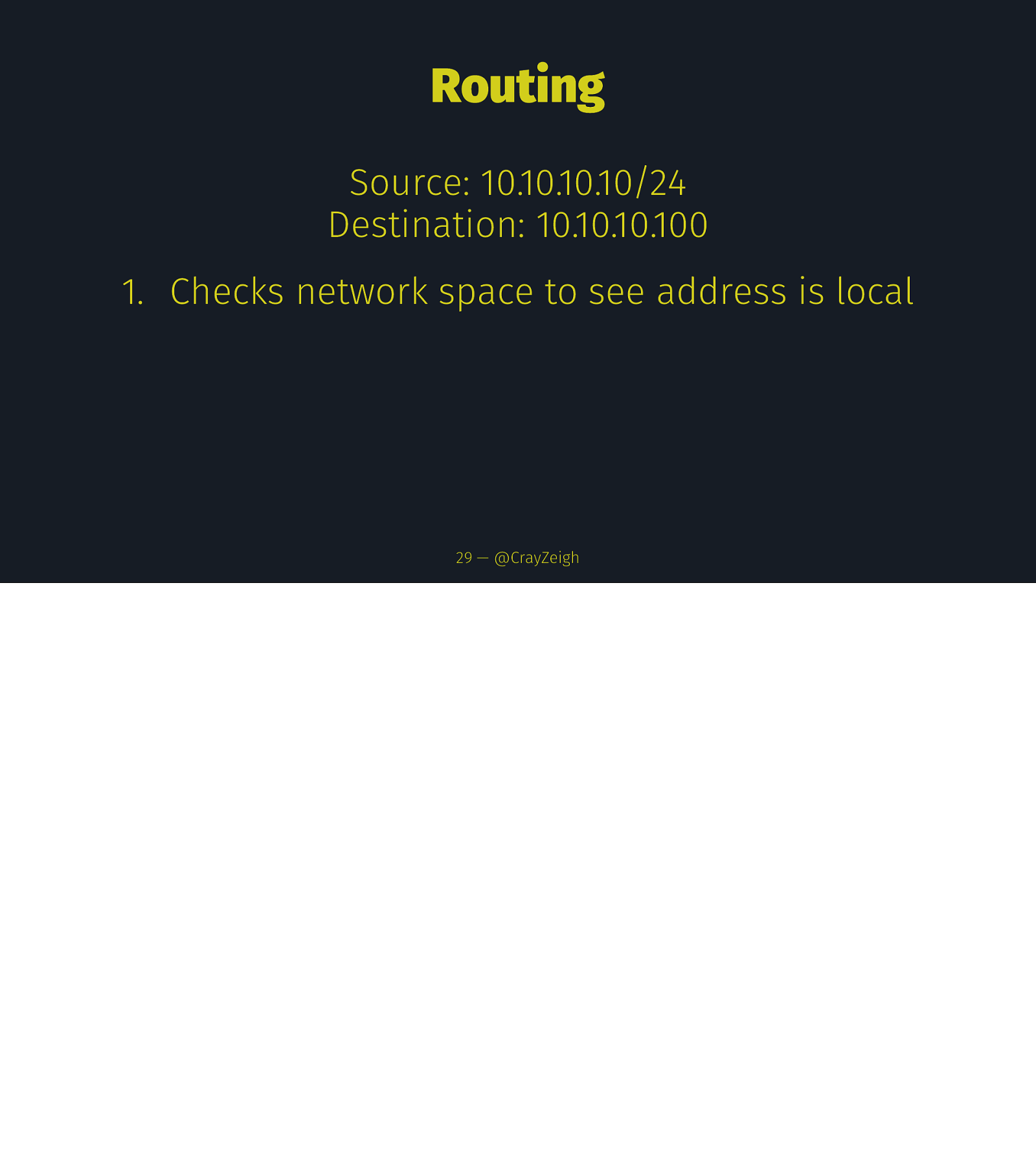
Routing Source: 10.10.10.10/24 Destination: 10.10.10.100 1. Checks network space to see address is local 29 — @CrayZeigh
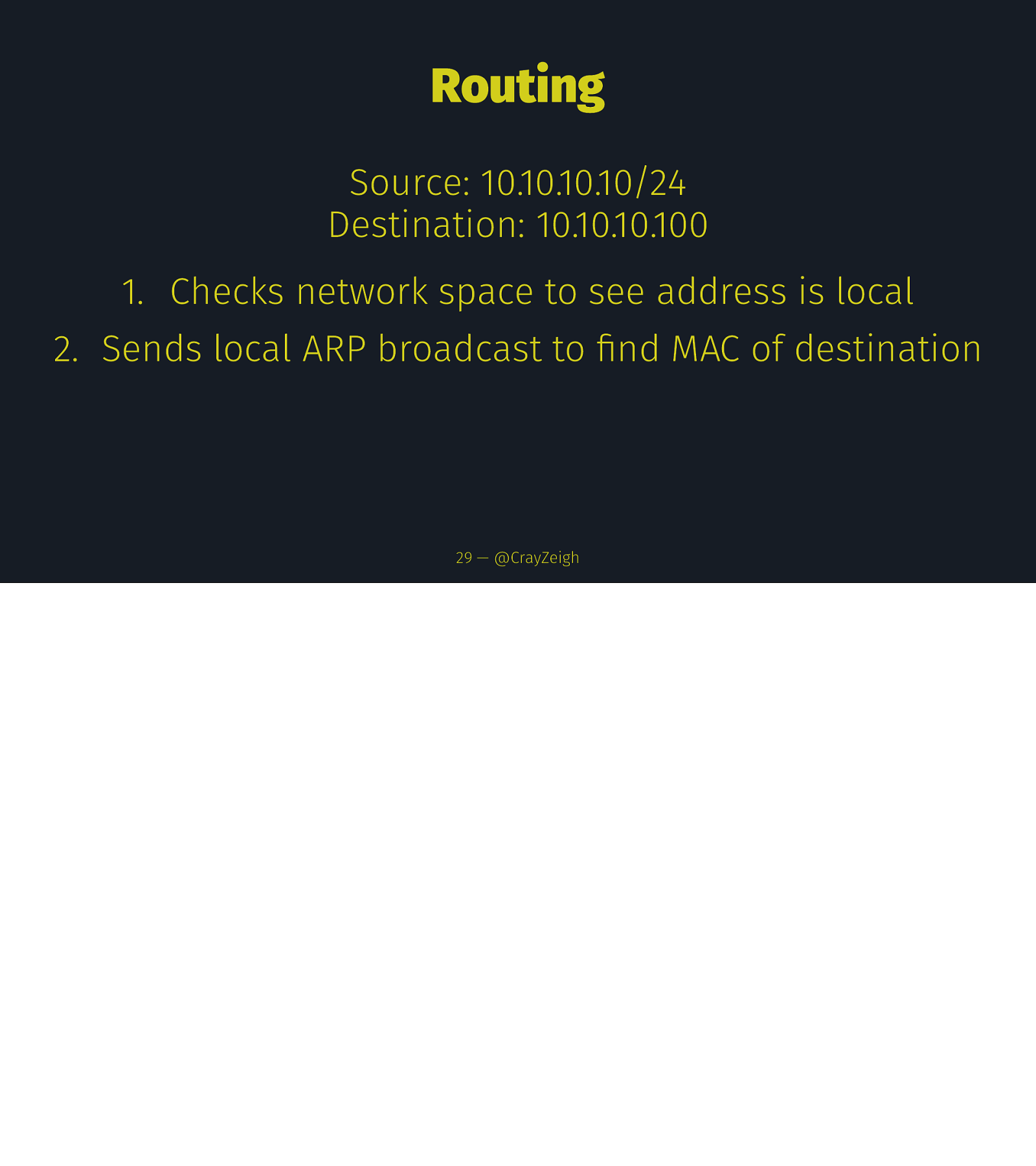
Routing Source: 10.10.10.10/24 Destination: 10.10.10.100 1. Checks network space to see address is local 2. Sends local ARP broadcast to find MAC of destination 29 — @CrayZeigh
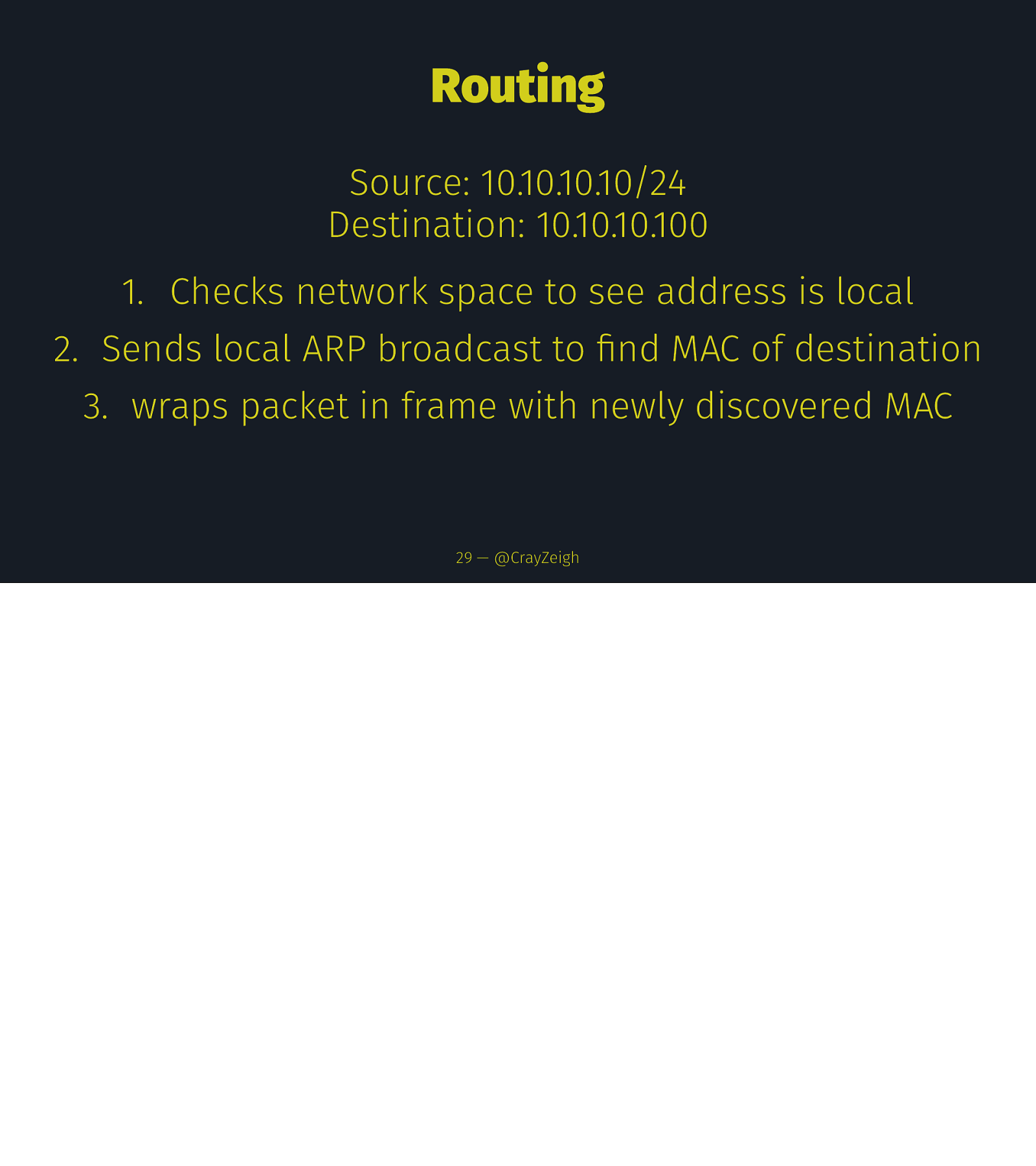
Routing Source: 10.10.10.10/24 Destination: 10.10.10.100 1. Checks network space to see address is local 2. Sends local ARP broadcast to find MAC of destination 3. wraps packet in frame with newly discovered MAC 29 — @CrayZeigh
Routing Source: 10.10.10.10/24 Destination: 10.10.10.100 1. Checks network space to see address is local 2. Sends local ARP broadcast to find MAC of destination 3. wraps packet in frame with newly discovered MAC 4. sends data frame through switch to destination “directly” 29 — @CrayZeigh

Routing Source: 10.10.10.10/24 Destination: 1.1.1.1 30 — @CrayZeigh
Routing Source: 10.10.10.10/24 Destination: 1.1.1.1 1. Checks network space and see’s address is remote 30 — @CrayZeigh
Routing Source: 10.10.10.10/24 Destination: 1.1.1.1 1. Checks network space and see’s address is remote 2. Forwards packet to the local router (usually default gateway) through switch 30 — @CrayZeigh
Routing Source: 10.10.10.10/24 Destination: 1.1.1.1 1. Checks network space and see’s address is remote 2. Forwards packet to the local router (usually default gateway) through switch 3. Wraps packet in frame with router’s mac address and desired destination’s IP 30 — @CrayZeigh
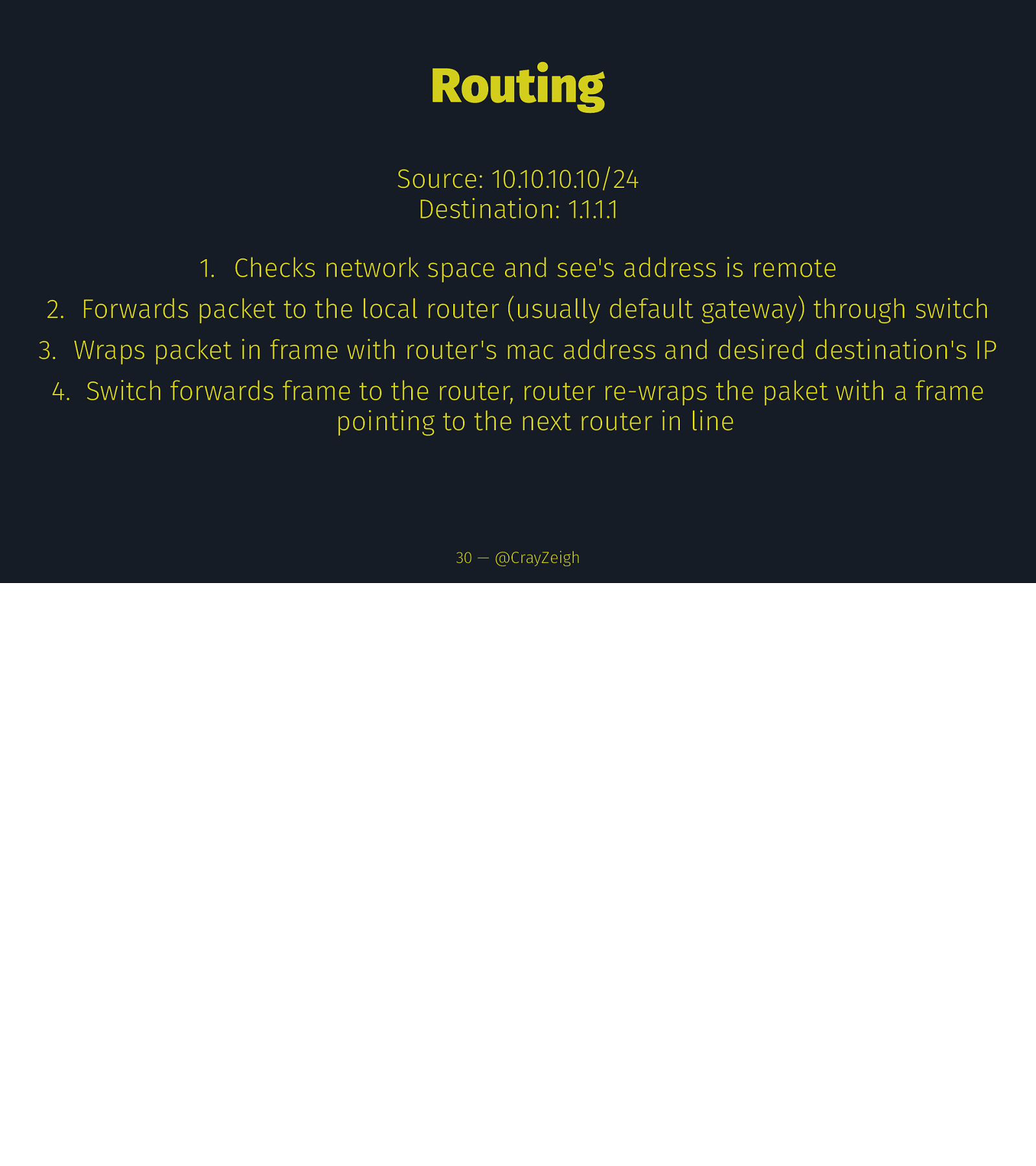
Routing Source: 10.10.10.10/24 Destination: 1.1.1.1 1. Checks network space and see’s address is remote 2. Forwards packet to the local router (usually default gateway) through switch 3. Wraps packet in frame with router’s mac address and desired destination’s IP 4. Switch forwards frame to the router, router re-wraps the paket with a frame pointing to the next router in line 30 — @CrayZeigh
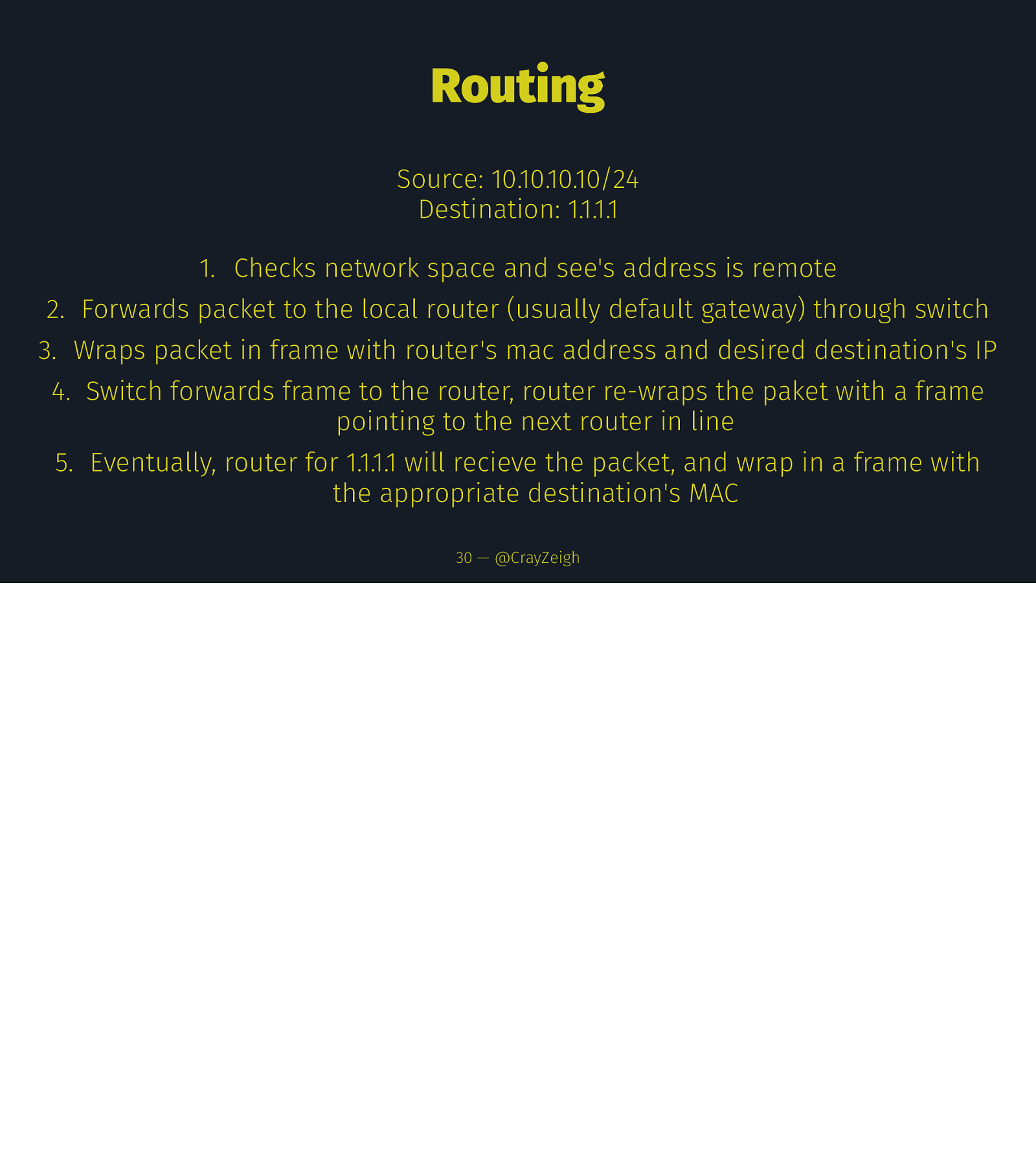
Routing Source: 10.10.10.10/24 Destination: 1.1.1.1 1. Checks network space and see’s address is remote 2. Forwards packet to the local router (usually default gateway) through switch 3. Wraps packet in frame with router’s mac address and desired destination’s IP 4. Switch forwards frame to the router, router re-wraps the paket with a frame pointing to the next router in line 5. Eventually, router for 1.1.1.1 will recieve the packet, and wrap in a frame with the appropriate destination’s MAC 30 — @CrayZeigh

How does the router know where the next stop is? Routing Tables 31 — @CrayZeigh
How does the router know where the next stop is? Routing Tables → (also used locally on your hosts) 31 — @CrayZeigh
How does the router know where the next stop is? Routing Tables → (also used locally on your hosts) → 3 general types of routes 31 — @CrayZeigh
How does the router know where the next stop is? Routing Tables → (also used locally on your hosts) → 3 general types of routes → Connected (networks assigned to router interfaces) 31 — @CrayZeigh
How does the router know where the next stop is? Routing Tables → (also used locally on your hosts) → 3 general types of routes → Connected (networks assigned to router interfaces) → Static (manually set, default gateway usually) 31 — @CrayZeigh

How does the router know where the next stop is? Routing Tables → (also used locally on your hosts) → 3 general types of routes → Connected (networks assigned to router interfaces) → Static (manually set, default gateway usually) → Learned (Shared with peers, BGP) 31 — @CrayZeigh

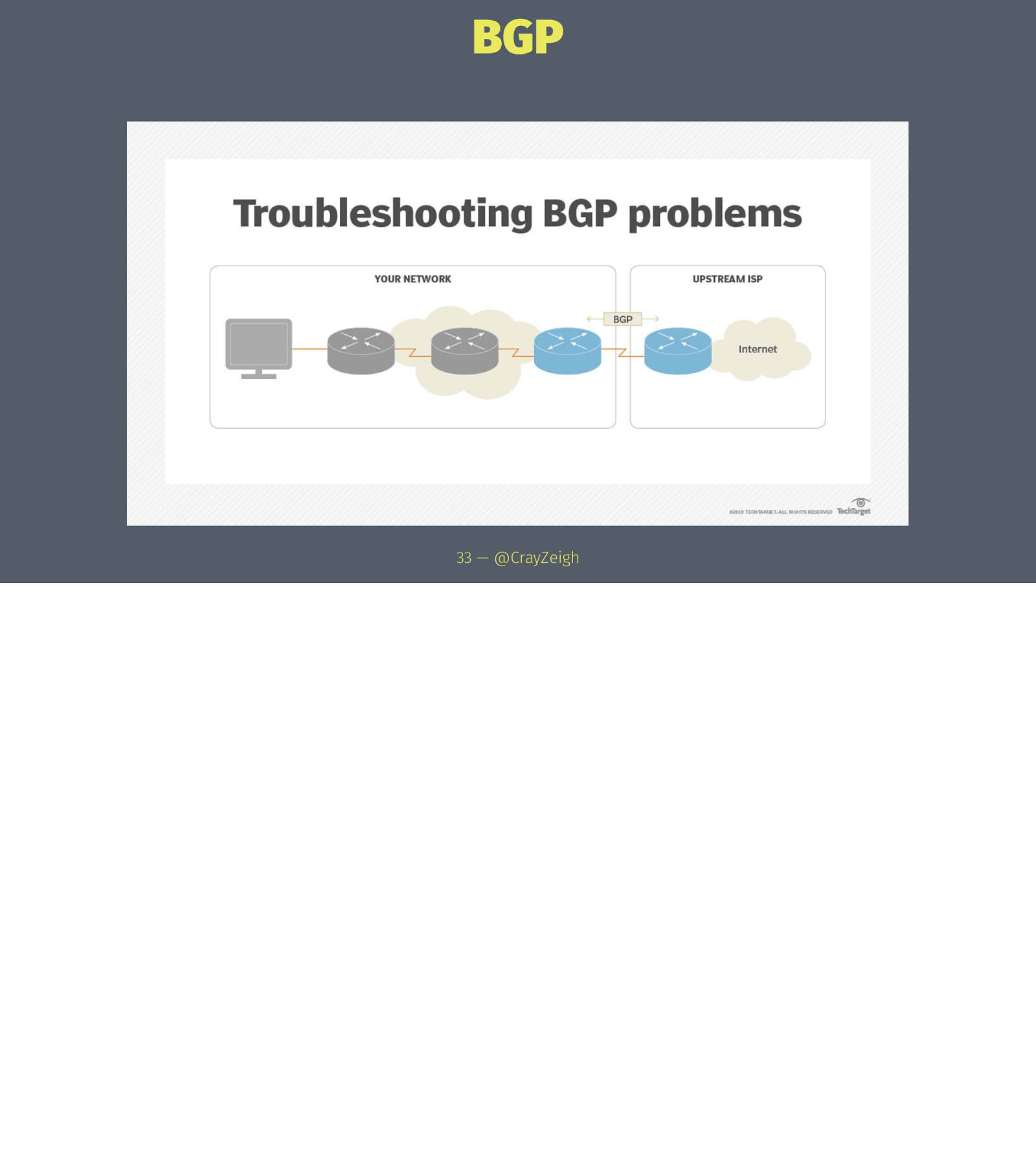
BGP Border Gateway Protocol 32 — @CrayZeigh

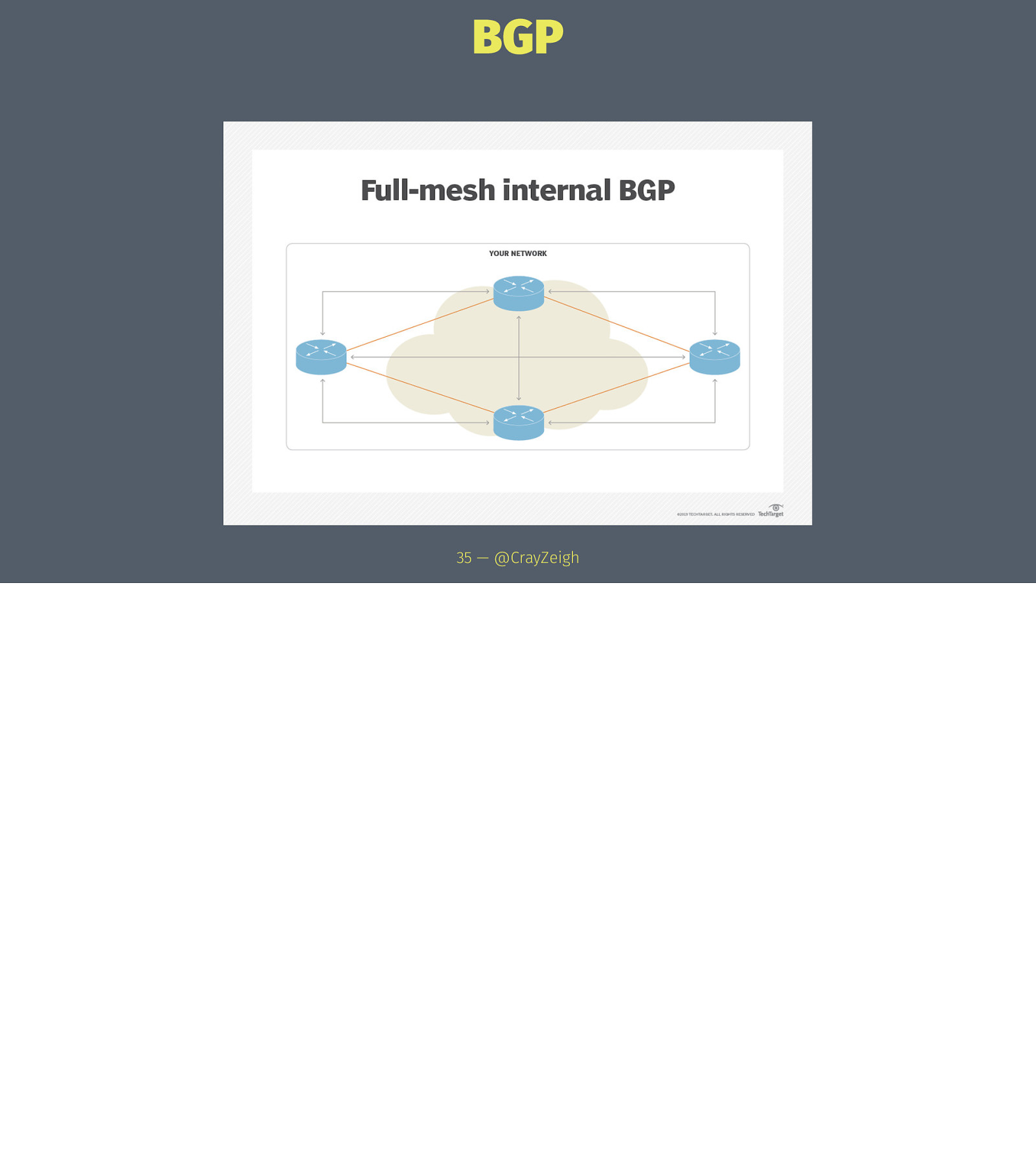
BGP Border Gateway Protocol → Advertises routes between (TCP) peered Autonomous Systems 32 — @CrayZeigh

BGP Border Gateway Protocol → Advertises routes between (TCP) peered Autonomous Systems → Routes can be aggregate “supernets” to save table space 32 — @CrayZeigh

BGP Border Gateway Protocol → Advertises routes between (TCP) peered Autonomous Systems → Routes can be aggregate “supernets” to save table space → Helps determine “best” route to destination since multiple routes may contain the same prefixes 32 — @CrayZeigh

BGP Border Gateway Protocol → Advertises routes between (TCP) peered Autonomous Systems → Routes can be aggregate “supernets” to save table space → Helps determine “best” route to destination since multiple routes may contain the same prefixes → Leveragable for anycast/edge performance increases 32 — @CrayZeigh
BGP 33 — @CrayZeigh

BGP 34 — @CrayZeigh
BGP 35 — @CrayZeigh
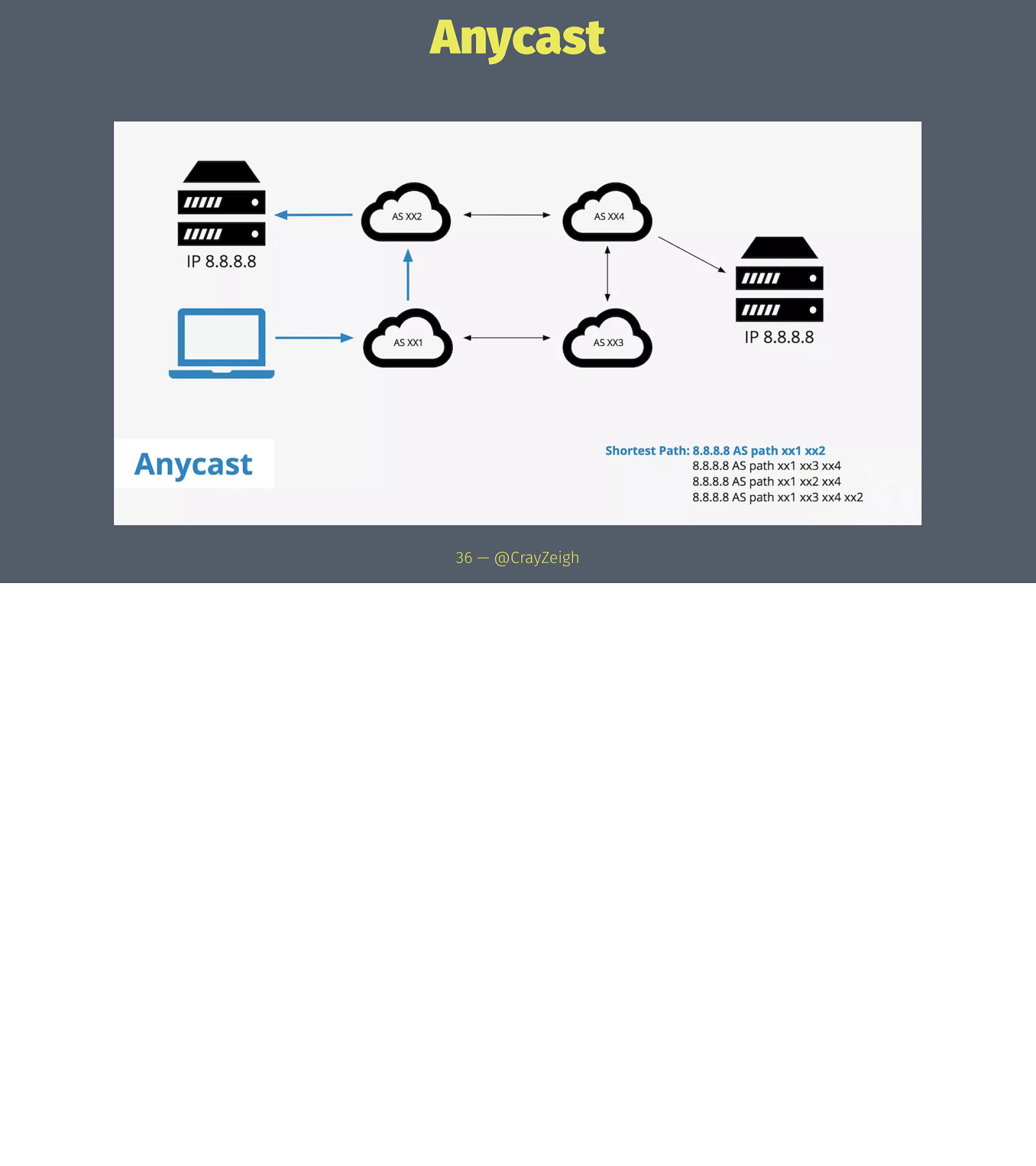
Anycast 36 — @CrayZeigh
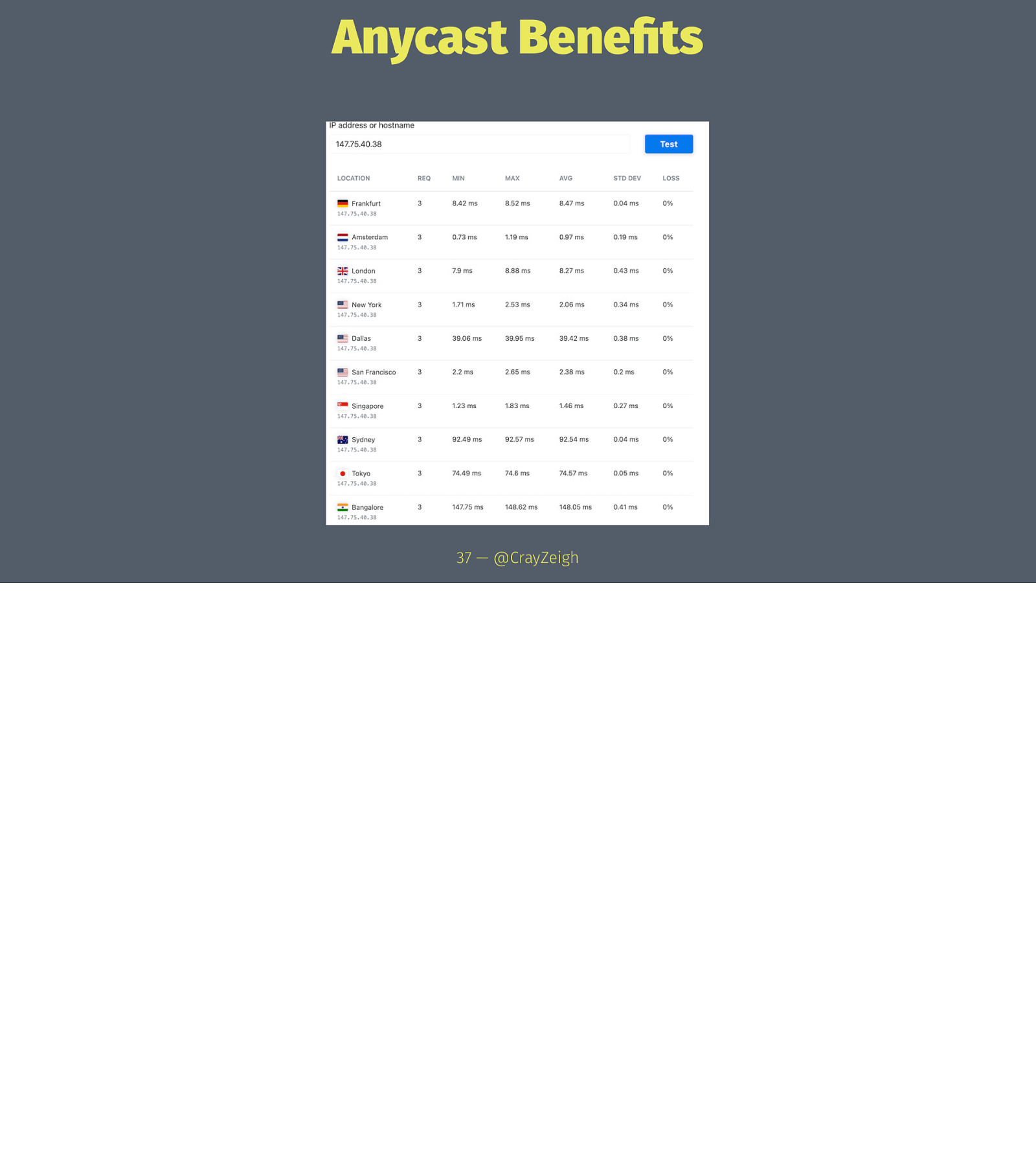
Anycast Benefits 37 — @CrayZeigh
What happens when you visit a website? 38 — @CrayZeigh
Hi! ! I’m Aaron dev advocate: organizer: sometimes host: Twitter: @CrayZeigh Slides: speaking.crayzeigh.com 39
40 — @CrayZeigh
As with all modern computing, the network stack has gotten increasingly abstracted away as we move to cloud services and cloud native infrastructure, but underneath it all, we’re still trying to accomplish the same things as always, get data from one system to another as quickly and efficiently as possible without interruption or eavesdropping. Starting with the classic interview question, “What happens when you try to access a website from your computer?” this talk reviews the modern complexity of the internet and reminds us about how some functional routing, switching and firewall knowledge can help us untangle the modern messes generated by layers of abstraction. We’ll start with some things like, “what about before I even get an IP address” and end up talking about BGP, the routing protocol that runs the internet. You’ll leave with a better understanding of what’s actually happening after you apply your chosen network settings to your cluster or hyperscaler, and a better framework for understanding how your cloud native applications and services are communicating across the web.
